IN THIS ARTICLE
Table of Contents
Comprehensive data security and customer data privacy are essential requirements in today’s dynamic remote work environment. Collaborating with a Chicago BPO company introduces expert solutions for navigating the challenges of the digital era.
Chicago businesses must understand the significance of secure outsourcing in protecting sensitive information and fostering trust in an increasingly interconnected landscape.
This guide discusses remote work data security, its importance to companies, and strategies to enforce it. It also explains how outsourcing can boost its efficiency.
Keep reading to learn more.
What is Remote Work Data Security?

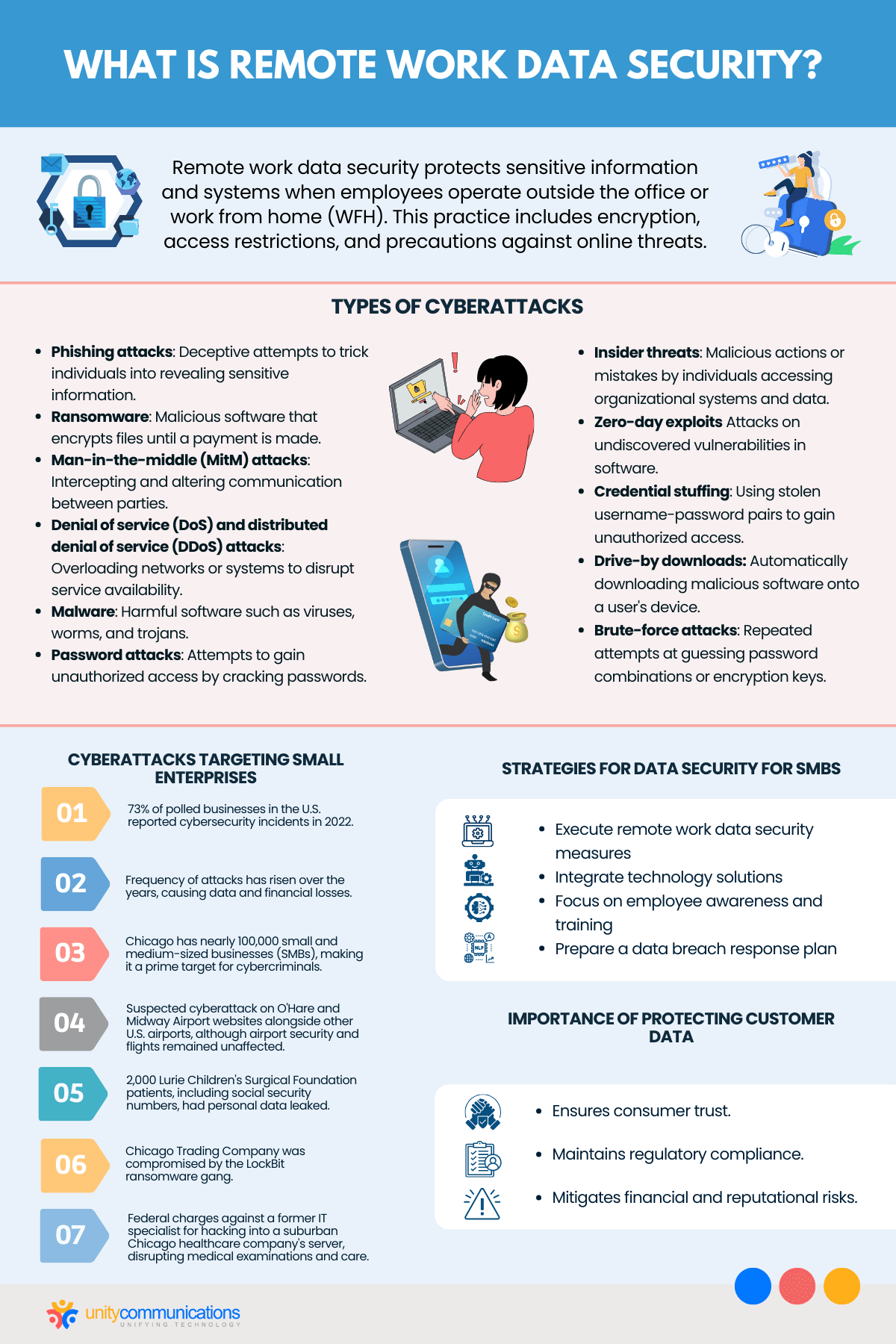
Remote work data security protects sensitive information and systems when employees operate outside the office or work from home (WFH). This practice includes encryption, access restrictions, and precautions against online threats.
The following cyberattacks can harm or compromise remote work data and online security systems:
- Phishing attacks are deceptive attempts to trick individuals into revealing sensitive information through fraudulent emails, messages, or websites.
- Ransomware is malicious software that encrypts files, often crippling systems and data access, until a payment is made for their release.
- Man-in-the-middle (MitM) attacks involve intercepting and altering communication between two parties, compromising data integrity and confidentiality.
- Denial of service (DoS) and distributed denial of service (DDoS) overload a network or system to disrupt service availability.
- Malware is software designed to harm or exploit systems, including viruses, worms, and trojans.
- Password attacks are attempts to gain unauthorized access by cracking passwords through brute force or dictionary attacks.
- Insider threats are malicious actions or inadvertent mistakes by individuals accessing the organization’s systems and data.
- Zero-day exploits are attacks on undiscovered vulnerabilities in software before they are fixed, posing a significant risk.
- Credential stuffing involves using stolen username-password pairs to gain unauthorized access to other accounts due to password reuse.
- Drive-by downloads automatically download malicious software onto a user’s device when they visit a compromised website.
- Brute-force attacks are repeated attempts at guessing password combinations or encryption keys until the correct one is found.
Remote Work Data Security: Crucial for Chicago Businesses
Data security enables Chicago businesses to safeguard sensitive information from cyberattacks. Protecting customer data ensures consumer trust and regulatory compliance, mitigating financial and reputational risks. Companies and organizations in the Windy City have experienced recent cyberattacks. Among them:
- Illinois fell victim to a ransomware attack exploiting a third-party file transfer system vulnerability. Cybersecurity agencies attribute the incident to the CL0P ransomware gang.
- The O’Hare and Midway Airport websites experienced a suspected cyberattack alongside other U.S. airports. Despite the disruption, the City of Chicago’s Department of Aviation assured that airport security and flights remained unaffected.
- 2,000 Lurie Children’s Surgical Foundation patients had personal data, including social security numbers, leaked to an unidentified group.
- The Chicago Trading Company reportedly suffered a compromise by the LockBit ransomware gang. This incident occurred days after the gang admitted to being responsible for an attack on ICBC Financial Services’s website.
- According to the indictment, a former IT specialist faces federal charges for hacking into a suburban Chicago healthcare company’s server. This attack disrupted medical examinations and care for multiple individuals.
Hackers are also increasingly targeting small enterprises in the U.S., with 73% of polled businesses reporting cybersecurity incidents in 2022. The frequency of attacks has risen over the years, causing data and financial losses for many. Chicago has almost 100,000 small and medium-sized businesses (SMBs), making the city a prime target for cybercriminals.
Strategies for Remote Work Data Security for Chicago SMBs

Microenterprises, startups, and small organizations can implement remote work data security strategies to protect customer, client, and company data. Consider the following approaches:
Execute Remote Work Data Security Measures
Ensuring robust remote work data security is imperative for Chicago companies. They must adopt comprehensive measures to safeguard sensitive information. A multifaceted approach to fortifying digital assets and maintaining organizational data integrity includes the following standards:
- Encryption. Data encryption is fundamental to remote work security. It protects data from unauthorized access by converting it into unreadable code. End-to-end encryption safeguards data confidentiality from sender to recipient and emphasizes the importance of secure digital environments.
- Secure access controls. Establishing specific access controls limits data access to authorized personnel. Role-based access assigns permissions based on job roles, reducing risks. Multi-factor authentication (MFA) also strengthens controls by requiring users to provide multiple forms of identification.
- Virtual private networks (VPNs). VPNs offer a secure remote connection for employees accessing organizational networks from diverse locations. They encrypt user-system communication, reducing interception risk. Adhering to best practices optimizes functionality, addresses vulnerabilities, and enhances overall security.
- Regular security training. Human factors often account for significant risks in data security. Comprehensive training educates employees on best practices, such as phishing awareness. Sessions provide knowledge to identify and thwart phishing attempts, reducing cyberattack vulnerability.
Integrate Technology Solutions
Sophisticated technology solutions must be embraced to enhance organizational defenses. These methods offer a holistic strategy for combating emerging threats, emphasizing endpoint devices and cloud settings. Explore some techniques:
- Utilize advanced security software. Robust antivirus and anti-malware solutions are a frontline defense for detecting, quarantining, and eliminating malware. Use endpoint security for this involves remote intrusion detection, firewalls, and device management. Update software regularly to enhance agility and counter emerging threats.
- Leverage cloud-based solutions. Securing cloud-stored data involves encryption for data protection, access controls, and identity management. To enhance security, apply best practices such as regular auditing and a robust incident response plan. These ensure adherence to industry standards.
Focus on Employee Awareness and Training
In cybersecurity, employees are the frontline guardians against potential remote work data security threats. Thus, Chicago businesses must cultivate a vigilant, well-informed workforce ready to respond to emerging dangers. Discover how to develop staff technical knowledge:
- Foster employee awareness. Human vulnerability is a crucial cybersecurity risk, highlighting the critical importance of employee awareness. Launch cybersecurity training programs to educate employees on evolving threats, instill responsibility, and empower them to recognize and thwart potential cyberattacks.
- Conduct periodic training sessions. Regular, dynamic cybersecurity training ensures workers are updated on the latest threats and protective measures. These sessions include practical scenarios and simulations, fostering a culture of cybersecurity consciousness.
Prepare a Data Breach Response Plan
An elaborate response strategy to a data breach helps a business navigate difficulties in remote work data security. This approach can reduce the impact of a cyberattack while also strengthening trust and credibility with end users, clients, and stakeholders. Consider the following pointers:
- Develop a comprehensive incident response plan. It must include identification, containment, eradication, recovery, and learning strategies. This document evolves with emerging threats, outlining roles, communication channels, and tools. Regular drills prepare the response team for effective mitigation.
- Collaborate with cybersecurity experts in case of a breach. Work with external experts during a data breach. Align response plans, ensure clear communication, and clarify roles and responsibilities. Integrate the experts into drills for seamless coordination, establishing secure and unified information-sharing protocols.
- Establish communication protocols with customers and stakeholders. Transparent communication is vital in addressing the fallout of a data breach. Clear protocols with customers and stakeholders ensure timely information dissemination regarding breach resolution steps and risk mitigation.
Outsourcing Strengthens Remote Work Data Security for Chicago SMBs

Entrusting remote work data security to service providers with WFH professionals is more practical for Chicago SMBs than deploying strategies internally. Check out how business process outsourcing (BPO) providers can help:
- Cost-efficient operations. For many SMBs, establishing and maintaining an in-house cybersecurity team can be financially burdensome. Outsourcing offers a cost-effective solution with predictable budgeting and fixed costs.
- Advanced technology solutions. Third-party providers invest in cutting-edge security technologies that might be financially challenging for smaller businesses to implement in-house. These tools ensure a higher level of protection against sophisticated cyberattacks.
- Accessible specialized expertise. Outsourcing to cybersecurity experts provides SMBs with technical knowledge and skills in remote work data security. These professionals are dedicated to staying informed about the latest threats and security trends.
- 24/7 monitoring and support. Outsourcing partners can offer continuous tracking and assistance, providing SMBs with round-the-clock surveillance against potential threats. Immediate response to incidents helps mitigate risks to business continuity.
- More focus on core competencies. Outsourcing data security responsibilities allows SMBs to concentrate on their core business. In-house teams can focus on strategic initiatives while leaving the complexities of cybersecurity to third-party experts.
- Scalable operations. Outsourcing provides flexibility in scaling security measures based on the needs of SMBs. This adaptability ensures that the cybersecurity strategy aligns with evolving requirements.
- Greater compliance assurance. BPO organizations specialize in compliance, aiding SMBs with industry-specific regulations and ensuring data security surpasses legal standards.
- Rapid implementation of security measures. Outsourcing enables rapid deployment without the delays associated with hiring and training an in-house team.
- Shared responsibility. Collaboration with a cybersecurity partner means shared duties for data security. This approach fosters a proactive and comprehensive defense against cyber threats.
Safeguarding Customer Data Through Outsourcing
Why consider outsourcing call center, data security, technical support, and other services to a BPO provider? The main reasons are improved efficiency, greater expertise, better cost savings, and increased scalability.
BPO companies also provide specialized services such as cybersecurity, research and analytics, quality assurance and testing, and contact center as a service (CCaaS) solutions.
Outsourcing customer data security ensures customer trust and loyalty, regulatory compliance, and resilience against cyberattacks, supporting long-term business development.
Chicago SMBs should consider the following steps when outsourcing remote work data security to nearshore or offshore BPO providers to protect customer data effectively:
Assess Security Needs
Before outsourcing, businesses must evaluate their remote work data security needs. The following methods help assess security requirements:
- Identify and categorize the sensitivity of handled data. Distinguish between confidential customer information and nonsensitive data to prioritize security measures.
- Conduct a comprehensive risk analysis. This review helps determine potential threats and vulnerabilities. It covers data storage, transmission, and access points, providing a holistic view of security risks.
- Align with data protection regulations and industry compliance standards. Verify that the security measures meet or exceed legal requirements, mitigating the risk of regulatory penalties.
- Perform a gap analysis to identify weaknesses. Pinpoint areas of improvement in current security infrastructure to enhance overall data protection.
- Review and refine user access controls. Implement the principle of least privilege to restrict access to sensitive data, minimizing the risk of unauthorized exposure.
Define Security Objectives
Determining security goals guides comprehensive strategies and ensures effective measures to protect valuable customer data. Check out the following ways to define security objectives:
- Specify the primary data protection goals. The targets must include preventing unauthorized access, ensuring data integrity, and maintaining confidentiality.
- Set specific targets for mitigating the identified risks. Whether reducing vulnerabilities or enhancing incident response, articulate measurable objectives for enhanced security.
- Define objectives for improving user access controls. Emphasize the principle of least privilege. Specify the level of access allowed for each employee to minimize potential breaches.
- Establish encryption objectives for data at rest and in transit. Define the encryption standards and methodologies, ensuring a secure data environment.
- Set objectives for strengthening authentication mechanisms. Consider implementing MFA to bolster user identity verification.
- Outline objectives for incident response readiness. Define response times, communication protocols, and measures for continuous improvement in handling security incidents.
- Identify exact targets for employee training programs. Set goals for increasing awareness about cybersecurity threats, mainly focusing on preventing phishing and social engineering.
- Establish objectives for security audits of remote work processes. Define the frequency and scope of audits to ensure ongoing adherence to security standards.
Select Vendors
When outsourcing remote work data security, choosing the correct partner is significant. Consider the following factors:
- Security expertise. Pick experts in remote work security. Evaluate their history of implementing solid measures, including encryption, access controls, and threat detection.
- Compliance adherence. Prioritize vendors committed to stringent compliance with data protection laws and industry-specific regulations, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act of 1996 (HIPAA).
- Experience in remote work support. Look for vendors with experience in supporting remote work environments. They must be familiar with secure communication channels, VPNs, and other remote work data security tools.
- Customization capabilities. Choose vendors that can customize solutions for specific remote work data security needs, ensuring alignment with your business requirements.
- Incident response preparedness. Review vendors’ incident response plans to assess their readiness for security breaches. A strong strategy for identifying, containing, and mitigating incidents is crucial for remote work data security.
- Reputation and track record. Evaluate vendors’ reputations through client testimonials and reviews. A proven track record in data security implementation signals reliability and competence.
- Communication. Opt for vendors emphasizing transparent communication for collaborative and prompt resolution of security concerns.
- Scalability and flexibility. Select vendors with scalable and flexible solutions to accommodate your business’s growth. Scalability ensures that data security measures can adapt to changing business requirements.
- Training programs. Consider vendors that prioritize continuous training programs for their staff. Regular training ensures the vendor’s team stays up-to-date on the latest security threats and best practices.
- Data handling practices. Assess the vendor’s practices for data processing, storage, and transmission. Robust methods adhering to industry standards ensure sufficient remote work data security.
Build a Secure Infrastructure
After selecting the outsourcing partner, develop a secure infrastructure tailored to the identified needs for a fortified remote work environment. Check the details below:
- Encryption protocols. Apply strong encryption for data in transit and at rest to guarantee the confidentiality and security of customer data during transmission and storage.
- Access controls. Enforce strict access controls for sensitive customer data, incorporating role-based and least privilege principles in the design of access systems.
- Authentication mechanisms. Implement MFA for added user authentication security, requiring an extra verification step in case credentials are compromised.
- VPNs. Deploy secure VPNs for encrypted connections in remote work settings, safeguarding data transmission from potential interception.
- Security training. Provide regular security training for workers, emphasizing adherence to protocols and threat recognition.
- Phishing awareness programs. Conduct regular simulations to educate workers on phishing threats and help them avoid such attempts.
Monitor and Audit Continuously
Outsourced data security requires constant surveillance and reporting. Regular evaluations and audits guarantee that security measures remain effective and adaptive to new threats. Follow these tips:
- Conduct regular security audits. Perform security checks on the outsourced processes to identify potential vulnerabilities. Frequent assessments help address security weaknesses proactively.
- Track data handling practices. Monitor how the outsourcing partner handles, processes, and transmits customer data. This ongoing scrutiny ensures that data handling practices align with established security protocols.
Establish Communication Protocols
Setting smooth and straightforward interactions with the BPO partner guarantees transparent and timely information dissemination during security incidents. This ensures a unified and effective response to threats.
Here are the two communication methods:
- Internal communication channels. Define communication channels within the business and with the outsourcing partner. Clearly outline responsibilities and escalation procedures to facilitate swift communication.
- External communication strategies. Develop communication strategies for customers, stakeholders, and regulators during a data breach. Transparent and timely communication maintains trust and compliance.
The other benefits of clear communication protocols include:
- Enhanced team coordination. Improved collaboration promotes cohesive teamwork, enabling members to share insights and address challenges more effectively.
- Efficient problem resolution. Collaborative protocols enable quick issue identification and resolution through clear information exchange among team members.
Improve and Adapt
The ever-changing cybersecurity landscape requires organizations and their outsourcing partners to constantly adjust and develop. Examine and update security procedures, policies, and training programs regularly to remain ahead of new threats. Consider the following recommendations:
- Technology upgrades. Stay informed about technological advancements and upgrade security technologies accordingly. This includes updating encryption algorithms, security software, and other protective measures.
- Training program evolution. Evolve training programs to address emerging threats. Regularly educate employees and outsourcing partners about the latest cybersecurity best practices.
- Regulatory compliance updates. Stay updated on data protection laws and changes in regulatory requirements. Ensure that security measures and practices align with the latest compliance standards.
The Bottom Line
The dynamic business landscape requires vigilant measures. To succeed, Chicago SMBs must prioritize remote work data security and safeguard customer data through outsourcing.
BPO companies employ expert solutions, enabling businesses to focus on core functions. A proactive data security approach mitigates risks, ensuring sustained trust and resilience in the digital era.
Let’s connect to learn more about outsourced remote work data security for Chicago businesses!





