IN THIS ARTICLE
Table of Contents
Despite the cost-effectiveness of business process outsourcing (BPO), clients might have security concerns over confidential information and intellectual property. Challenges related to patents, trademarks, and trade secrets can result in copyright infringement and brand identity theft.
Hence, businesses must understand how intellectual property rights work when outsourcing. Such insights enable them to strengthen their copyright protection while enjoying the strategy’s cost-cutting benefits.
This article explores everything you must know about intellectual property before entering into an official outsourcing partnership.
The Importance of Protecting Intellectual Property Rights
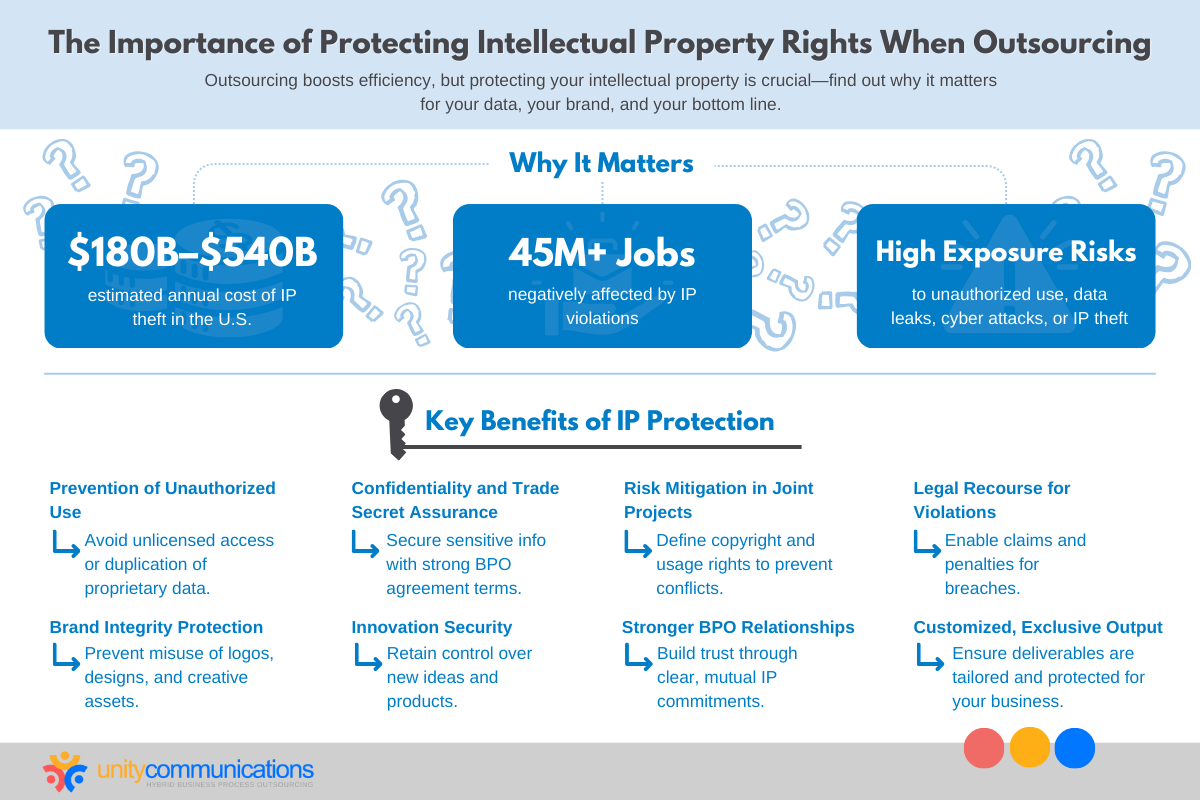
Outsourcing agreements offer significant cost savings and increased productivity. However, the intellectual property of your products and services must remain a top concern, especially when outsourcing software development and marketing functions.
Businesses increasingly rely on BPO companies for streamlined operations. However, the remote nature of outsourcing transactions makes sensitive data more susceptible to cyberattacks. Potential intellectual property risks are also more pronounced.
The latest statistics show that the cost of intellectual property theft falls between $180 billion and $540 billion annually in the United States alone. These incidents have also negatively impacted more than 45 million jobs in the country.
Keeping intellectual property safe while outsourcing is critical to avoiding such hefty consequences. Doing so lets you experience the following benefits:
- Prevent unauthorized use or replication. Outsourcing requires you to share sensitive data with third parties. A joint intellectual property protection guide avoids unlicensed access or duplication of proprietary technologies, processes, or creative works.
- Maintain confidentiality and trade secrets. A well-structured BPO agreement includes robust measures to prevent data leaks that could harm both parties’ competitiveness.
- Mitigate risks in collaborative projects. For example, application and brand development projects involve intellectual property concerns regarding finished products. Clearly defining copyright ownership and usage rights through legal agreements helps prevent disputes and misunderstandings.
- Ensure legal protection in cases of violations. Safeguarding intellectual property rights allows you to seek damages against your BPO partner in case of contractual breaches.
- Secure brand image and reputation. Well-defined intellectual property measures strengthen your brand’s integrity and competitive advantage. They help avoid the misuse of your logos and assets, which can harm your credibility and weaken consumer trust.
- Drive innovation without compromise. Companies sometimes leverage outsourcing to innovate and produce specialized products, such as official enterprise apps. Intellectual property protections help avoid losing control over groundbreaking ideas.
- Improve business relationships. Clear intellectual property protection strategies build trust between your in-house and third-party teams. This is particularly important for long-term projects to attain success.
- Customize specific enterprise needs. You outsource tasks to obtain outcomes tailored to your requirements, such as personalized customer service. Securing intellectual property pushes your BPO partner to generate output exclusive to your business.
Ways to Safeguard Intellectual Property When Outsourcing

Exploring what BPO is involves understanding ways to protect your intellectual property. Safeguard your company’s innovative ideas and products by exercising the following practices:
Know the Types of Intellectual Property Involved in Outsourcing
Identifying the types of intellectual property associated with BPO transactions lets you know how to best secure your brand assets. It guides you in establishing ownership rights, usage permissions, and restrictions on accessing proprietary information.
Different intellectual property categories are subject to specific rules and regulations. Thus, you can also use this knowledge to ensure your provider complies with relevant legal frameworks to avoid disputes and penalties.
Tailor your risk mitigation strategies by understanding the kinds of intellectual property commonly related to outsourcing, such as:
- Copyright secures original works of authorship, such as software code, written content, music, and multimedia. Piracy of these materials could potentially cause $113 billion in revenue loss.
- Trademarks protect original goods and services’ symbols, names, and slogans. This is crucial to preserving brand identity when outsourcing.
- Patents grant inventors exclusive rights to their discoveries for a limited period. This intellectual property is relevant for outsourced research and development projects involving novel technologies.
- Trade secrets refer to classified business data, such as product formulas, processes, or customer lists. Protecting trade secrets while working with a provider strengthens your competitive edge.
- Confidential information comprises any non-public data that holds value for enterprises. This information includes business plans, financial reports, and customer data shared during BPO engagements.
- Utility patents protect new or improved products, processes, or machines for 20 years. Patent owners can create, use, or sell their inventions. However, they may be required to pay for maintenance fees.
- Software licenses allow businesses to use, modify, or distribute software. This authorization determines how the client can use or distribute third-party software.
- Domain names serve as addresses for websites. Considerations around domain names may arise when a BPO company manages your web development or online presence.
- Geographical indications safeguard products linked to a specific region. They are necessary when providers produce exclusive products tied to a particular country.
- Mask works keep the design of semiconductor chips safe from tampering. They are necessary when outsourcing the manufacturing of electronics and computer systems.
Conduct Due Diligence
Performing due diligence before signing a contract helps you identify the BPO company that meets your intellectual property requirements. This proactive approach guides you in addressing outsourcing risks beforehand.
Due diligence helps identify and categorize all relevant intellectual property assets the BPO company can reliably hold. This measure ensures both parties have clear ownership rights and reduces the risk of conflicting claims and legal complications.
Protect your intellectual property rights by exercising the following methods:
- Determine the BPO project’s scope. Identify the specific intellectual property to be shared or developed throughout the contract duration.
- Develop an inventory of your existing intellectual property assets. This comprehensive list may include trademarks, copyrighted materials, patented inventions, and trade secrets within your organization.
- Review your existing business documents to identify copyright ownership. Clarify your intellectual property ownership and what you can share when outsourcing. This step helps set restrictions on using your proprietary information when working with a provider.
- Request and evaluate the provider’s intellectual property policies. As you screen potential vendors, ask about the confidentiality measures they implement to protect your sensitive business information.
- Assess the employment contracts of workers who will join your project. Ensure third-party workers have signed provisions related to intellectual property protection and confidentiality.
- Inspect the provider’s security measures. These practices should include information technology (IT) protection strategies, data storage protocols, and system access controls. A robust cybersecurity framework is vital to safeguard intellectual property and avoid wasting $4.45 million due to a breach.
- Confirm the vendor’s compliance with relevant rules and regulations. Ensure the service provider adheres to critical intellectual property laws, including industry-specific and international standards. This step helps prevent potential misunderstandings or conflicts of interest.
- Examine past intellectual property-related issues before outsourcing. Investigate whether the BPO provider was involved in legal disputes regarding copyright, patents, or data compromises. Check for past litigation indicating a lack of security commitment.
- Request references and case studies. Seek opinions and recommendations from the provider’s previous clients, especially those with projects similar to yours. Ask for evidence of the vendor’s ability to safeguard intellectual property and meet confidentiality requirements.
- Understand technology transfer protocols. Be familiar with the rules for sharing and securing technology assets when adopting IT outsourcing. Clarify with your potential BPO partner how to manage ownership and usage rights for software code, algorithms, or technical know-how.
Clarify Intellectual Property Terms and Conditions
Specifying intellectual property terms and conditions in an outsourcing contract or service-level agreement (SLA) ensures both parties know how confidential enterprise information is used. Such clarity prevents misunderstandings and guarantees a successful and secure BPO partnership.
Furthermore, this step helps avoid the high cost of legal fees and operational delays due to unexpected conflicts. It lets you maximize the benefits of hiring a provider. Learn how to write an SLA that highlights intellectual property protection below:
- Identify who owns the intellectual property involved in a project. Determine whether you or your BPO partner will retain full licensing rights for created or used assets. You may also consider a joint ownership arrangement.
- List the deliverables to be considered intellectual property. This list is crucial for collaborative projects involving custom software development and creative content. Be specific about what you will own and what may have shared licensing.
- Outline the specific usage rights granted to the service provider. Detail whether the vendor can handle your intellectual property exclusively or non-exclusively. Include the scope and boundaries of those rights.
- Articulate confidentiality and non-disclosure provisions. Your SLA should enumerate ways to keep sensitive information confidential. Consider relevant data privacy rules while setting each team’s obligations.
- Address subcontractors. If your BPO partner plans to engage subcontractors, elaborate on managing intellectual property rights. Ensure the main outsourcing agreement’s terms and conditions also apply to third parties.
- Define technology transfer protocols to protect software code. Explain in the contract how to conduct and document the transfer. Remember to include any restrictions on further dissemination.
- Incorporate intellectual property-related indemnification clauses. Describe each team’s responsibilities in cases of infringement claims. This action helps distribute the financial burden for legal defense and damages equally.
- Include mechanisms for resolving intellectual property disputes. Outline the step-by-step procedures for handling conflicts of interest or breaches of terms. Guidelines could include arbitration, mediation, or settlement.
- Determine which regulatory laws apply to the BPO contract. State the governing law that applies to the intellectual property terms and conditions. This way, you know how to resolve disputes correctly.
- Spell out contract termination clauses. Determine the steps for handling intellectual property upon closing the BPO agreement. Clarify the process of returning or destroying confidential data and transferring ownership rights. Include other post-termination obligations related to intellectual property.
To ensure the contract is precise and legally sound, consult with regulatory experts focused on intellectual property in outsourcing. These professionals provide valuable insights and recommendations for navigating complex legal considerations. They help match the provider’s protection goals with yours.
Remember to sign a non-disclosure agreement (NDA) and your finalized SLA. NDAs prevent the theft of sensitive data and business assets and strengthen the protection of your intellectual property rights.
Establish Data Residency Requirements
Data residency requirements help safeguard intellectual property when outsourcing, especially with an international service provider. Different regions have varying laws on this matter. These prerequisites ensure the BPO company complies with your country’s legal framework.
Here’s how to establish data residency requirements:
- Understand data protection laws relevant to your industry and BPO arrangement. Familiarize your in-house and third-party teams with the policies and procedures related to data residency, cross-border data transmission, and intellectual property security.
- Identify data residency requirements based on the collected insights. Some governments mandate companies to retain certain data types within their geographic location or jurisdiction. Consider this factor when developing prerequisites with the BPO company.
- Specify on-premises data storage locations. Specify the physical locations where your BPO partner can store and process your enterprise information. Designate specific servers, data centers, or regions where your provider can maintain and process the information.
- Add data residency clauses to contracts. Outline the requirements and authorized locations for data storage and processing. These factors should align with legal standards while considering your BPO vendor’s operational needs and limitations.
- Plan for data transfer protocols when exchanging data between jurisdictions. Define the mechanisms and tools to be used for the transmission. Ensure these resources comply with relevant data protection laws, minimizing the risk of unauthorized access during worldwide transfers.
- Determine penalties for non-compliance with data residency requirements. Incorporate the violation terms and fees in your SLA should the BPO provider fail to adhere to the agreed-upon terms. Emphasize ways to settle disputes when data and intellectual property breaches occur during outsourcing.
- Develop data retention and deletion policies. Work closely with the provider to set the duration for retaining and securely deleting sensitive information when no longer needed. This safeguard helps prevent data breaches and unauthorized access.
- Stay informed of changes in data protection laws and industry standards. Regularly update your data residency requirements according to the latest trends. Doing so guarantees ongoing compliance with evolving regulations.
- Keep pace with tech advancements related to data security and residency. Implement updated technologies and best practices to enhance intellectual property and sensitive data protection.
Implement Access Controls
Implementing robust access controls is critical for protecting intellectual property rights in outsourcing. According to Verizon’s 2022 report, 82% of these breaches involved a human element. Employees’ database misconfigurations or input mistakes enable cybercriminals to enter and exploit their employers’ systems.
To combat this threat, deploying access controls regulates who can use your sensitive information to accomplish crucial tasks. It reduces the risk of unauthorized disclosure or misuse.
Let the following points guide you in this crucial matter:
- Define different access levels based on job roles and responsibilities. Determine personnel who need access to specific types of intellectual property and confidential data. These positions include administrators, developers, or project managers.
- Utilize role-based access control (RBAC) to assign permissions per job function. This tool allows BPO workers to complete tasks without unnecessary privileges. It distributes duties that meet the outsourcing project’s specific intellectual property and data requirements.
- Comply with the least privilege principle. This principle gives regular workers the minimum access necessary to conduct their duties. Avoid granting broad permissions that could expose confidential data to unnecessary risks.
- Execute robust user identity verification methods. These include multi-factor authentication, passwords, biometrics, and facial recognition. Combine these techniques with proper authorization rules to only grant access to authenticated users.
- Perform regular reviews of access rights. This approach ensures that permissions match current BPO roles and responsibilities. Update access controls promptly when job positions or team structures change.
- Use access control lists (ACLs). Both parties can use an ACL to specify and grant users or system processes access to confidential data and business assets. The list provides granular control over essential files and directories.
- Encrypt data in transit and at rest. This security technique protects intellectual property during transactions and storage. Even if unauthorized parties access the data, it remains safe and unreadable without proper permission.
- Execute controls to oversee user sessions effectively. Enforce session timeouts to automatically log users out after a period of inactivity. This method lessens the risk of unauthorized data access if a user forgets to log out or leaves a session unattended.
- Set up comprehensive audit trails to track and record user activities. Frequently review audit logs to monitor and address suspicious or unauthorized access attempts. Optimize automated tools to provide real-time alerts for unusual activities.
- Implement masking and redaction techniques to secure sensitive data. These protective measures ensure that individuals with specific access rights see only the information necessary for their roles and responsibilities.
- Roll out vendor management controls. If outsourcing involves subcontractors, confirm that your BPO partner implements rules to manage their access effectively. Ensure that the subcontractor’s access aligns with the least privilege principles.
- Support regular security training for individuals with intellectual property access. Provide the necessary materials for your BPO partner’s training programs. Ensure third-party workers are aware of best practices to protect your sensitive information. Let them learn the consequences of unauthorized data access or disclosure.
- Implement robust endpoint security measures to safeguard devices. These include antivirus software, firewalls, and device encryption to stop unauthorized intellectual property access through compromised endpoints.
- Draft an incident response plan. Coordinate with your provider regarding the development of the strategy. Enumerate procedures to quickly investigate, contain, and mitigate the impact of security breaches.
- Perform security audits to evaluate the effectiveness of access controls. Require third-party security experts to conduct regular penetration testing and vulnerability assessments. These tests determine and address potential weaknesses in your critical systems.
Use Blockchain Technologies
Utilizing blockchain technologies helps strengthen the defense and preservation of your intellectual property rights when teaming with a BPO organization. These advanced tools offer a decentralized and tamper-resistant ledger system.
You can design the solution to allow selective disclosure of enterprise information. You and your BPO partner can maintain confidentiality while proving ownership or ensuring compliance with specific contractual terms.
This selective disclosure enhances privacy protection for sensitive intellectual property data. Here are some guidelines on how to use blockchain for this purpose:
- Understand blockchain basics. Familiarize yourself with the tech before beginning your blockchain implementation. Learn about its decentralized nature, cryptographic principles, and consensus mechanisms. These insights will help you effectively integrate blockchain into your intellectual property protection strategy when outsourcing.
- Develop a decentralized ledger for intellectual property assets. This ledger documents and organizes items, such as patents, trademarks, or proprietary files. It gives your in-house and third-party teams a comprehensive overview of confidential data that needs strict protection.
- Implement transparent ownership tracking systems. Blockchain records every change to licensing agreements. It provides an indisputable and evident history of intellectual property ownership.
- Incorporate timestamps in the ownership tracker. Blockchain has timestamping features that capture the creation, modification, and transfer of intellectual property assets per date and time. It provides an immutable and auditable timeline of events.
- Validate authenticity with cryptographic signatures. These electronic signatures verify the legitimacy of intellectual property assets when outsourcing. Linking these digital stamps to blockchain transactions ensures that confidential information is not altered and is traceable to the original owner.
- Facilitate automatic licensing and royalty payments. Blockchain-powered smart contracts automate licensing agreements and royalty payments throughout your BPO deal. These solutions automatically trigger and perform payment transactions based on predefined conditions when using, approving, or transferring intellectual property.
- Set up a decentralized blockchain storage for critical documents. Keeping significant intellectual property files safe in a dispersed manner strengthens security. This blockchain repository helps minimize the risk of unauthorized access or tampering.
- Enable interoperability with existing intellectual property management systems. The BPO company’s blockchain platform should seamlessly integrate with your current processes and systems. The integration simplifies the tech’s adoption without disrupting established in-house workflows.
- Team up with suppliers and stakeholders in a consortium blockchain. This shared infrastructure helps streamline intellectual property management in a BPO environment. It serves as a transparent and trusted platform for classified business data.
What If You Ignore Intellectual Property Security in Outsourcing?

The lack of intellectual property security when hiring BPO services leads to various drawbacks. Firstly, it weakens your competitive edge in the fast-paced market. Competitors or unauthorized parties that gain access to your proprietary data might use it to replicate your innovations, diminishing the uniqueness of your products and services.
An intellectual property breach damages your brand reputation and degrades your customer base. According to Salesforce’s latest statistics, 64% of consumers believe companies nowadays prioritize online privacy. They are likelier to continue doing business with a company that uses their data transparently.
Your customers may lose trust in your brand if they see any mishandling of their data, especially when seeking remote support. Hence, you must ensure your third-party customer service team meets your requirements for securing such confidential information.
Ultimately, the financial consequences of intellectual property infringement are high. Patent litigation processes usually cost from $2.3 million to $4 million. The legal proceedings last for one to three years before reaching trial, leading to substantial financial losses and operational delays on your end.
The Bottom Line
Entering a BPO partnership involves sharing confidential enterprise data. In addition to ensuring cost savings and efficiency, you must also protect your intellectual property rights when outsourcing. By understanding and exercising the key practices above, you can enjoy outsourcing’s long-term benefits.
Let’s connect if you still have questions regarding your intellectual property rights when acquiring outsourced services. As a certified service provider, Unity Communications has experts and comprehensive resources to help you understand how to protect your unique business assets and offerings amid an outsourcing arrangement.





