Table of Contents
Contact centers are pivotal in facilitating customer interactions, yet they demand stringent security measures for data protection.
According to Statista, incidents of data breaches surged to 125 million in 2020. Additionally, the Javelin Strategy highlighted that in 2021, 15 million Americans fell prey to identity theft.
This brings to light the importance of identity-centric security within contact centers. Implementing robust security protocols to safeguard identity data is crucial when hiring agents and utilizing a contact center as a service (CCaaS).
This article delves into the realm of identity-centered security for businesses. Continue reading to discover how your contact center can enhance its use of this vital security measure.
Understanding Identity-centered Security
Identity-centered security is part of cybersecurity and offline security and refers to measures focused on protecting customer and brand identity. These measures include authentication requirements, access control, network security, and more.
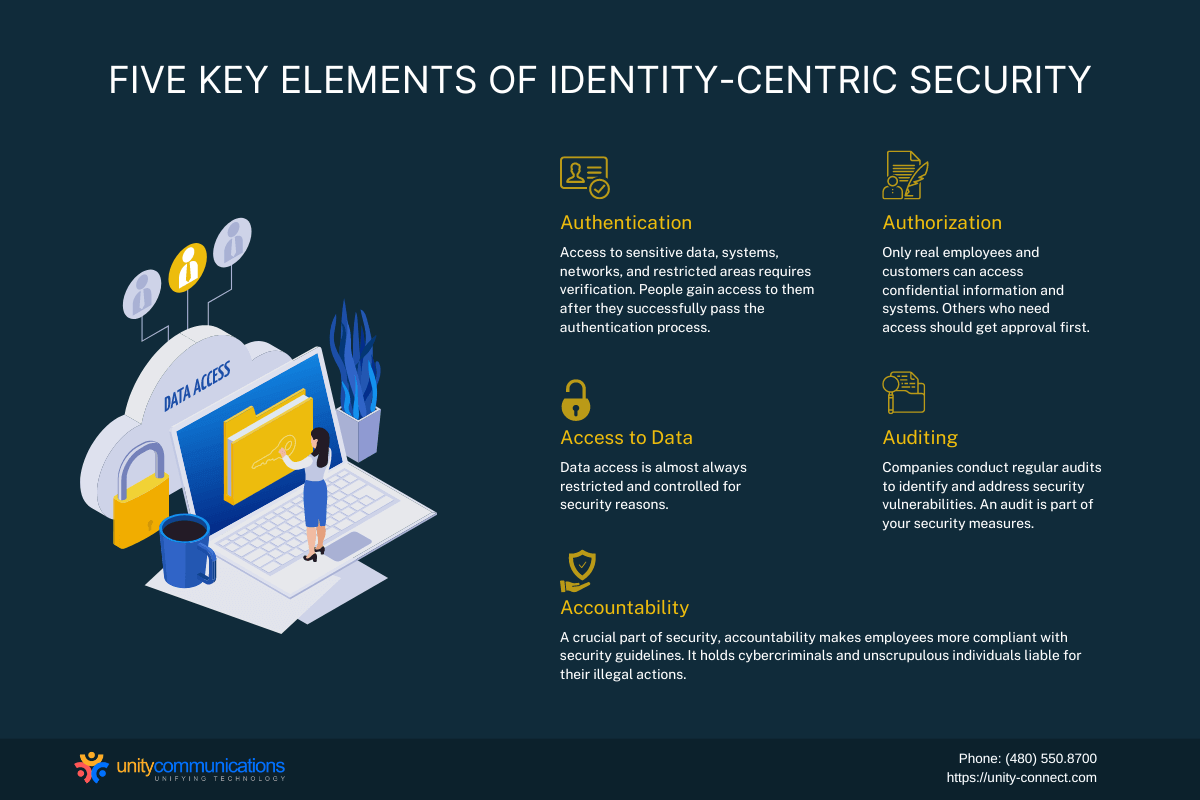
Five Key Elements of Identity-centric Security
Identity-centric security is the protection of humans and technologies from physical attacks or cyberattacks. It requires the five A’s as its key elements:
- Authentication: Access to sensitive data, systems, networks, and restricted areas requires verification. People gain access to them after they successfully pass the authentication process.
- Authorization: Only real employees and customers can access confidential information and systems. Others who need access should get approval first.
- Access to Data: Data access is almost always restricted and controlled for security reasons.
- Auditing: Companies conduct regular audits to identify and address security vulnerabilities. An audit is part of your security measures.
- Accountability: A crucial part of security, accountability makes employees more compliant with security guidelines. It holds cybercriminals and unscrupulous individuals liable for their illegal actions.
The Importance of Identity-centered Security for Contact Centers
Identity-centered security is crucial in contact center operations. Interactions between agents and customers usually happen via the web using a telecom network, and because contact centers handle sensitive information, the risk of identity fraud is high.
Now, let’s tackle data breaches and identity theft. Learn how identity-centric security protects contact center operations.
The Impact of Data Breaches and Identity Theft on Business
Statista said data breach cases in 2020 were the highest ever recorded. Fortunately, the number has decreased to approximately 52 million this year. But Javelin Strategy considers identity theft one of the fastest-growing criminal enterprises. In 2021, the cases cost about $52 billion, impacting nearly 42 million U.S. consumers.
Here’s the breakdown:
- Traditional identity fraud involves using consumer personal information for financial gain. Its losses reached $24 billion, affecting 15 million American consumers.
- New identity fraud entails influencing consumers to conduct transactions for financial gain. Its losses hit $28 billion, victimizing 27 million American consumers.
The statistics above prove the importance of business security. Companies of all sizes should have robust security measures to avoid data breaches. Specifically, they should focus on identity-centric measures to prevent identity theft.
How Identity-centric Security Protects Contact Center Operations
In contact centers, employees perform front-office functions by directly interacting with customers, usually via telecom networks that use the internet. They often deal with confidential consumer data, such as social security numbers and bank account details.
Identity-centered security is particularly vital for contact center operations. It controls data access and ensures data protection on hardware, software, or networks. Security measures guide employees in protecting information while interacting with customers. They work by combating the following cyberattacks:
- Password Attack: Cybercriminals hack passwords using password-cracking tools such as Aircrack and Abel. Make sure to enforce robust password requirements.
- Malware Attack: Cybercriminals infiltrate a network and steal data using malicious software such as worms, spyware, and ransomware. Secure your network by installing antivirus software, setting up firewalls, and updating your browsers.
- Phishing Attack: Cyberattackers pretend to be legitimate and send malicious emails. When victims click and open these emails, cyber attackers access sensitive information. Make sure to inform your employees about email protection.
- Man-in-the-middle Attack: Cyberattackers perform eavesdropping attacks. They penetrate communication between two parties to steal confidential information. Secure your network, encrypt devices, and avoid public Wi-Fi.
- SQL Injection Attack: This happens when hackers control the Standard Structured Query Language (SQL). They inject malicious codes into a database to reveal confidential data. Employ an intrusion detection system and perform validation of the user-supplied data.
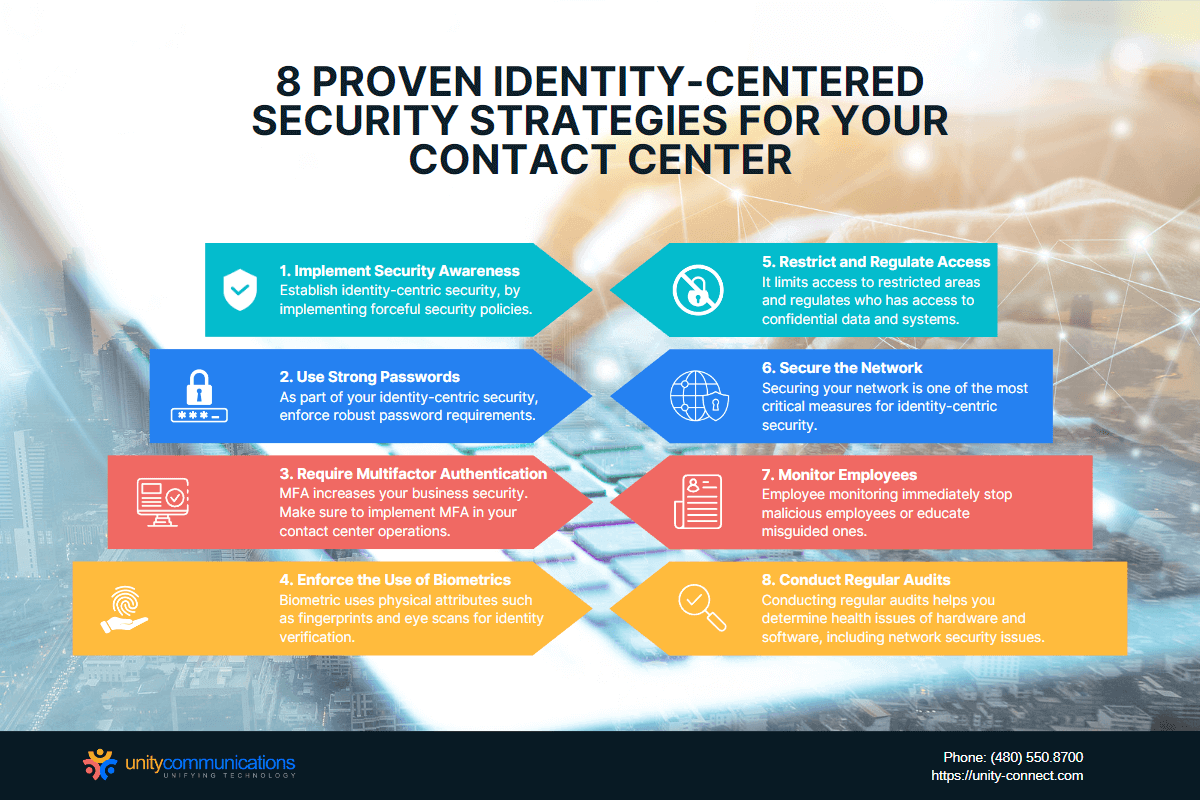
Eight Proven Strategies for Using Identity-centered Security for Your Contact Center
At this point, you know identity-centered security and how it works. More importantly, you understand why it is vital for your business.
Now, let’s discuss how your contact center can use identity-centric security.
1. Implement Security Awareness
Security is not the concern of your business leaders and IT staff; it is the concern of all employees. Your employees should take this seriously because they perform day-to-day tasks. Contact center agents should have security awareness as they work with customers directly.
To establish your identity-centric security, start by implementing forceful security policies. Make sure to orient and train your employees on these. Lastly, and most importantly, enforce these by holding everyone accountable.
2. Use Strong Passwords
According to TraceSecurity, over 80% of data breaches are due to poor password security. Almost 50% of employees admitted their company provides logins shared by several individuals. Also, 34% shared passwords with their team members and 32% with their managers.
As part of your identity-centric security, enforce robust password requirements. A strong password is easy to remember but difficult for others to guess. Microsoft says that a strong password has the following characteristics:
- At least 12 characters long
- Letters (lower and upper case), numbers, and symbols
- Words not found in the dictionary
- Not names, characters, products, or businesses
3. Require Multifactor Authentication
Multifactor authentication (MFA) is a multi-layered security measure for identity verification. It requires users to provide two pieces of evidence to gain access. Make sure to implement MFA in your contact center operations. For instance, have customers verify their account numbers first and then their dates of birth or the last four digits of the SSN.
MFA increases your business security. Having more than one verification item is better. Should one credential be compromised, unauthorized personnel still need to verify another. They will not get access if they fail to provide the correct information twice.
4. Enforce the Use of Biometrics
Identity refers to who you are as a user. Authentication involves verifying that you are who you claim to be. You usually enter your username and password to access data or systems.
Enforcing biometric use is best for your contact center operation. It uses physical attributes such as fingerprints and eye scans for identity verification. With this in place, only authorized employees can enter production.
5. Restrict and Regulate Access
Companies of all sizes now put premiums on access control. Its global market growth was worth $9.4 billion in 2022. It might reach $20.5 billion by 2032 at an 8.2% compound annual growth rate (CAGR).
Consider investing in access control as part of your identity-centered security. It limits access to restricted areas and regulates who has access to confidential data and systems. Ultimately, it’s a viable measure for enhancing your identity-centric security.
6. Secure the Network
Securing your network is one of the most critical measures for identity-centric security. But it is easier said than done. You have to consider many factors and do a lot of work. Here are some network security tips for your contact center operation:
- Install antivirus and anti-malware software
- Use or strengthen your firewall
- Set up a virtual private network (VPN)
- Update your firmware
- Consider Wi-Fi-protected access (WPA)
- Restrict Dynamic Host Configuration Protocol (DHCP)
- Use IPS and IDS
- Employ a reliable, secure sockets layer (SSL) certificate
- Back up your data
7. Monitor Employees
Employee monitoring should be part of your security measures. Track your contact center agents’ activities to ensure 100% security compliance. It can benefit you because it helps you:
- Track bad habits that will compromise your security and identity. You can correct these quickly.
- Identify internal threats. Upon discovery, you can immediately hold them accountable or terminate them.
- Immediately stop malicious employees or educate misguided ones.
8. Conduct Regular Audits
Identity-centered security requires regular audits. Do not conduct only one at the onset before taking measures. Conducting regular audits allows you to evaluate your current contact center operations. It also helps you determine:
- Vulnerability points
- Network security issues
- Health issues of hardware and software
- Scheduled maintenance and updates
- Employee security compliance
- Security technology upgrades
Assessing these as part of your audit ensures that you address issues as or before they arise and make the right security enhancements.
Five Key Benefits of Identity-centric Security for Contact Centers

Businesses with contact center operations should implement identity-centered security. Such security measures prove beneficial in a variety of ways, including:
- Robust Data Protection: Security measures help safeguard confidential information. Only contact center agents can access critical data, systems, and networks. They also protect customer identities. Only legitimate customers and authorized personnel have access to their accounts. Lastly, they prevent the cyberattacks mentioned above.
- Full Regulatory Compliance: Contact centers need to follow federal and state regulations. Consider information security (InfoSec) laws such as GLBA for financial protection and HIPAA for protected health information (PHI). Security measures ensure adherence to avoid legal implications and potential shutdown.
- Enhanced Organizational Efficiency: Establishing identity-centric security can streamline your authentication process, data management, and access control. Taking such security measures helps improve your organizational efficiency.
- Ensured Consumer Trust: Robust security equates to consumer trust. If you assure them of your security measures, they’re more likely to do business with you. Meanwhile, data breaches lead to customer distrust. They might escalate to customer complaints, legal ramifications, and a catastrophic business shutdown.
- Increased Profitability: Enhanced security translates to consumer trust. But its benefits go beyond this. Case in point: It has positive implications on your business profits. You’ll have consistent revenue if customers continue to do business with you.
The Bottom Line
Prioritizing identity-centered security is essential for every enterprise. This is especially true for front-office functions, which engage directly with customers.
For contact center operations, implementing an identity-centric security framework is crucial. It’s important to comprehend its mechanisms and prerequisites. Consider the suggested security strategies mentioned earlier when integrating this system into your business.
Such security not only safeguards data and ensures adherence to regulations but also enhances the organization’s overall efficiency. The end result? A boost in consumer confidence, which in turn, fosters business success. To explore how Unity Communications can assist your business in achieving these security goals, don’t hesitate to contact us.




